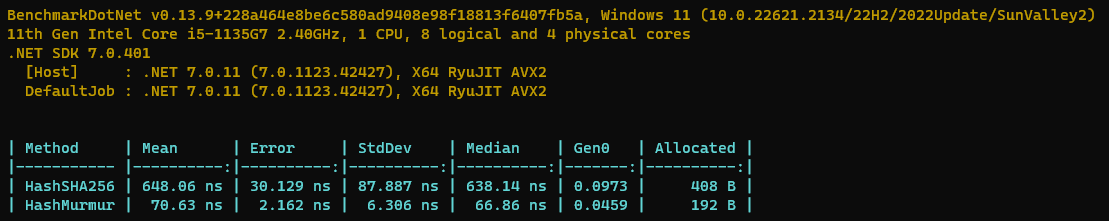
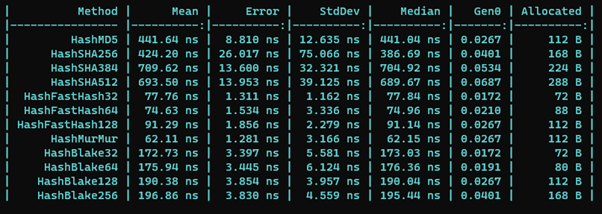
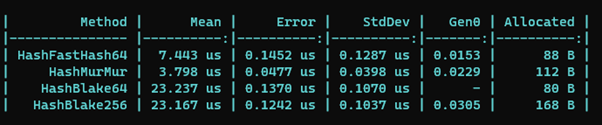
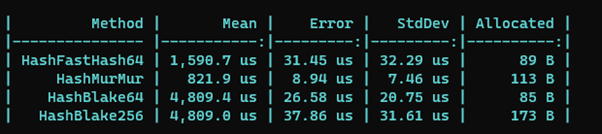
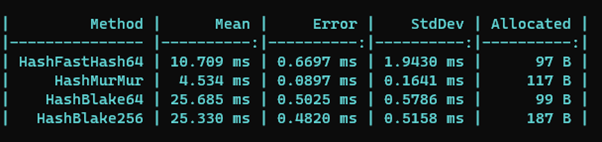
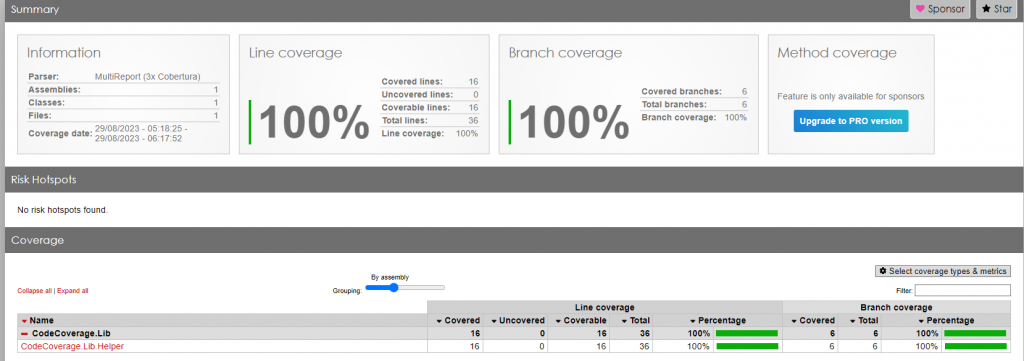
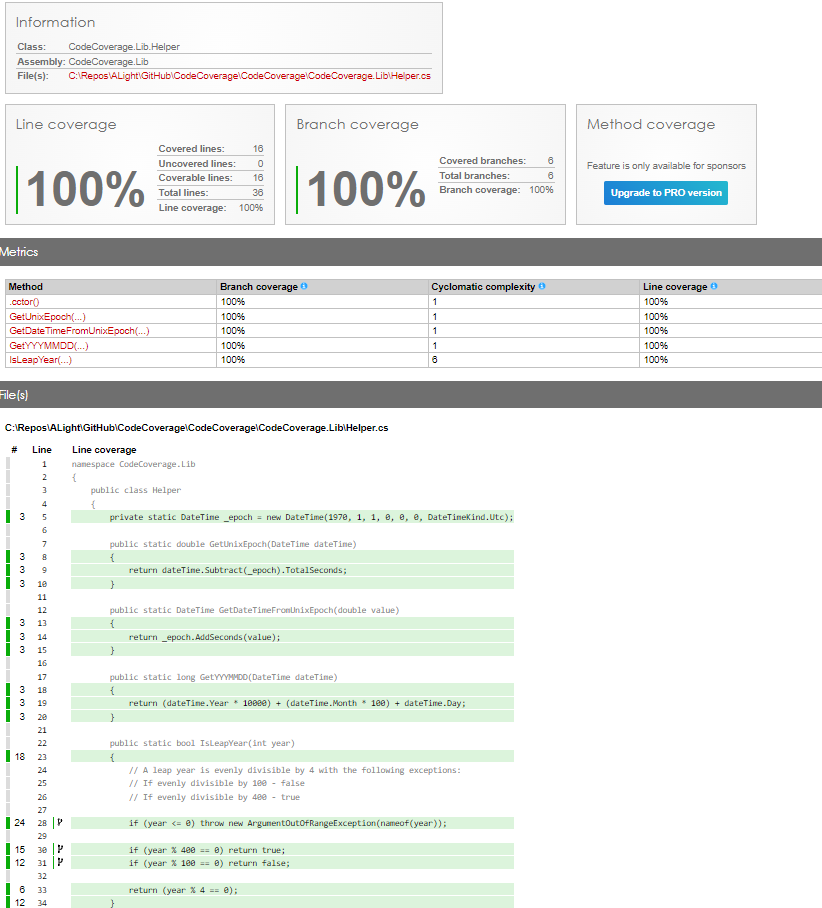
If you have access to Azure OpenAI services, the following code snippet shows how to chat with ChatGPT!
Some general tips:
- Secure your networks, i.e use private endpoints inside Azure! Stolen keys can be used by other people if the network is not secured.
This code example is C# version of what’s discussed in https://github.com/AzureCosmosDB/Azure-OpenAI-Python-Developer-Guide/blob/main/05_Explore_OpenAI_models/README.md
The above link is for Python developers, this blog post for C# developers.
var chatClient = new OpenAIClient(new Uri(azureEndPoint),
new AzureKeyCredential(apiKey));
var chatCompletionOptions = new ChatCompletionsOptions();
chatCompletionOptions.DeploymentName = "gpt35";
chatCompletionOptions.Messages.Add(new
ChatRequestSystemMessage("You are a helpful, fun and friendly sales assistant for Cosmic Works, a bicycle and bicycle accessories store."));
chatCompletionOptions.Messages.Add(new
ChatRequestUserMessage("Do you sell bicycles?"));
chatCompletionOptions.Messages.Add(new
ChatRequestAssistantMessage("Yes, we do sell bicycles. What kind of bicycle are you looking for?"));
chatCompletionOptions.Messages.Add(new
ChatRequestUserMessage("I'm not sure what I'm looking for. Could you help me decide?"));
var response = await
chatClient.GetChatCompletionsAsync(chatCompletionOptions);
if (response != null && response.Value != null &&
response.Value.Choices != null &&
response.Value.Choices.Count > 0)
{
System.Console.WriteLine(
response.Value.Choices.ElementAt(0).Message.Content);
}The above code has 3 configuration variables:
- azureEndPoint – This is the endpoint from Azure Portal.
- apiKey – One of the API keys from Azure Portal.
- The deployment name of the model that has been added through Azure Portal.
If the code was run successful, output looks like this:
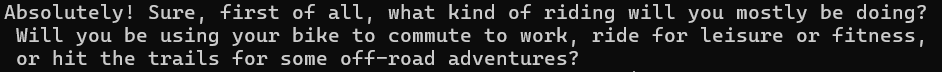
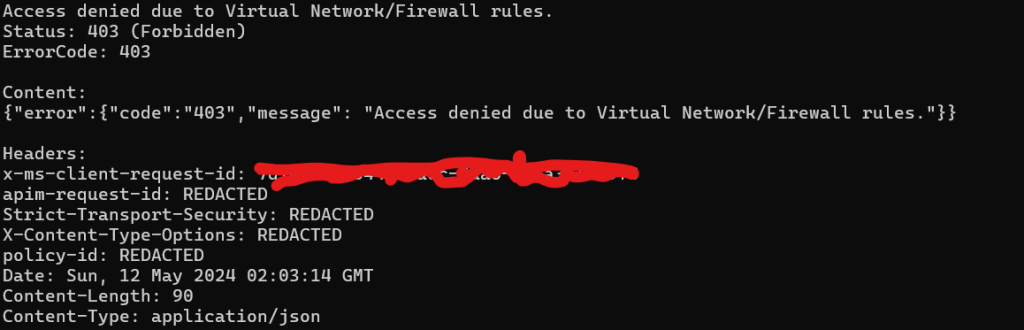
If there is network connectivity issues, there might be exceptions, if denied due to network security issues errors might be like the following:
–
Mr. Kanti Kalyan Arumilli

B.Tech, M.B.A
Founder & CEO, Lead Full-Stack .Net developer
ALight Technology And Services Limited
Phone / SMS / WhatsApp on the following 3 numbers:
+91-789-362-6688, +1-480-347-6849, +44-07718-273-964
kantikalyan@gmail.com, kantikalyan@outlook.com, admin@alightservices.com, kantikalyan.arumilli@alightservices.com, KArumilli2020@student.hult.edu, KantiKArumilli@outlook.com and 3 more rarely used email addresses – hardly once or twice a year.