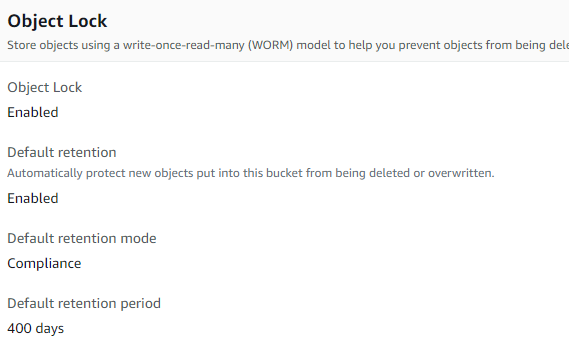
In my startup – ALight Technology And Services Limited, I don’t have any employees. I do everything myself. I know .Net web development. These other activities are something new for me.
Most of you know, I have been looking for secure, efficient way of accessing servers hosted in my AWS and Azure accounts. This effort is part of productionizing WebVeta and securing the servers.
I have written some blog articles about OpenVPN in the past and how-to automate changing keys using some C# code at random for higher security.
This blog post is about few other alternatives and some tips.
WireGuard is another free VPN software! But the problem 256-bit key. i.e less secure but high throughput. One possible way is by rotating the key on a timely basis. There is another software known as Pro Custodibus, that helps in rotating keys and managing keys + MFA!
OpenVPN is very highly configurable and can support 2048 bit keys and above.
How to easily install OpenVPN and some easy C# code snippets for Process class
The above blog post talks about how to install and use some C# code for re-generating server and client side keys. The above blog post allows keys + password protection for the ovpn file i.e 2 layers of higher security.
OpenVPN has the following interesting options for further security / monitoring and alerting:
--ipchange cmd
--route-up cmd
--route-pre-down cmd
--ping-exit n
--up cmd
--down cmd
--down-pre
--up-restart
--client-connect
--client-disconnect
--auth-user-pass-verify cmd method
--auth-gen-token [lifetime]
--single-session
Using some of these options and commands, alerts can be generated by either using scripts or programs. I would use C#, but any programming language or even shell scripts can be used.
Using –auth-user-pass-verify 3rd level of security can be added i.e an additional username + password security can be added.
–single-session allows one and only one session, no session re-negotiation – Probably perfect for my scenario.
TailScale is a very nice VPN management software and has a very generous free-tier of upto 100 devices and 3 users. With a little bit of custom programming and using TailScale the security can be increased and can be easily managed. However, one of the biggest problems I saw was registering servers. TailGate displays a URL in plain-text, the URL needs to be entered in browser and authenticated for registering a server in TailGate. If anyone knows the URL and if they authenticate before you, they can try to take-over the server and of-course you can immediately terminate server etc…
I think re-gistering servers should be 2 way i.e
- In the website allow copying some random GUID (don’t show the GUID in plain text).
- In the server after tailscale up, prompt for the GUID, treat the GUID like password, allow pasting but don’t echo the GUID.
- Generate another unique GUID on the server and display.
- User copies the server-side GUID and pastes in the website.
- Now pair the servers
Even if someone somehow steals the first GUID and pastes in their server, the second GUID generated by their server would be different and can’t be paired.
If someone steals the second guid, their browser-side first guid associated with their account would be different and can’t be paired.
Meanwhile TailScale pairing can be done little securely using my opensource tool – https://github.com/ALightTechnologyAndServicesLimited/LightKeysTransfer – This feature to be implemented, I would make an announcement when the feature gets implemented.
The feature would be very simple, instead of displaying the URL, the URL would be encrypted, use the client-mode part of tool for decrypting, copy and paste in small-sized browser window and approve.
This feature request has been submitted – https://github.com/tailscale/tailscale/issues/8823
–
Mr. Kanti Kalyan Arumilli

B.Tech, M.B.A
Founder & CEO, Lead Full-Stack .Net developer
ALight Technology And Services Limited
Phone / SMS / WhatsApp on the following 3 numbers:
+91-789-362-6688, +1-480-347-6849, +44-07718-273-964
kantikalyan@gmail.com, kantikalyan@outlook.com, admin@alightservices.com, kantikalyan.arumilli@alightservices.com, KArumilli2020@student.hult.edu, KantiKArumilli@outlook.com and 3 more rarely used email addresses – hardly once or twice a year.