Sometimes we need to access private repositories of a github account from linux servers for various purposes. For example, I have MFA enabled on my Github account, I need to clone a private repository inside a Linux server hosted in AWS. This article explains how to deal with such situations.
This is pretty much a re-hash of the steps provided in but in a slightly friendlier way.
Generating a new SSH key and adding it to the ssh-agent
Adding a new SSH key to your GitHub account
Login into your server and generate SSH keys by issuing the following command:
ssh-keygen -t ed25519 -C "<YOUR_EMAIL_ADDRESS>"You would be prompted for a filename, password and re-type password. You can accept the defaults and click enter or enter a separate filename and password.
Now start the SSH agent by issuing the following command:
eval "$(ssh-agent -s)"Now add the previously generated key for usage by issuing the following command:
ssh-add ~/.ssh/id_ed25519Now either copy the content of the public key by using the clip command or view the content of the public key by using the cat command:
clip < ~/.ssh/id_ed25519.pub
or
cat < ~/.ssh/id_ed25519.pubNow go to your GitHub account, sign-in and click on your profile on the right side top and click settings.
From the left menu click SSH and GPG Keys
Click New SSH Key
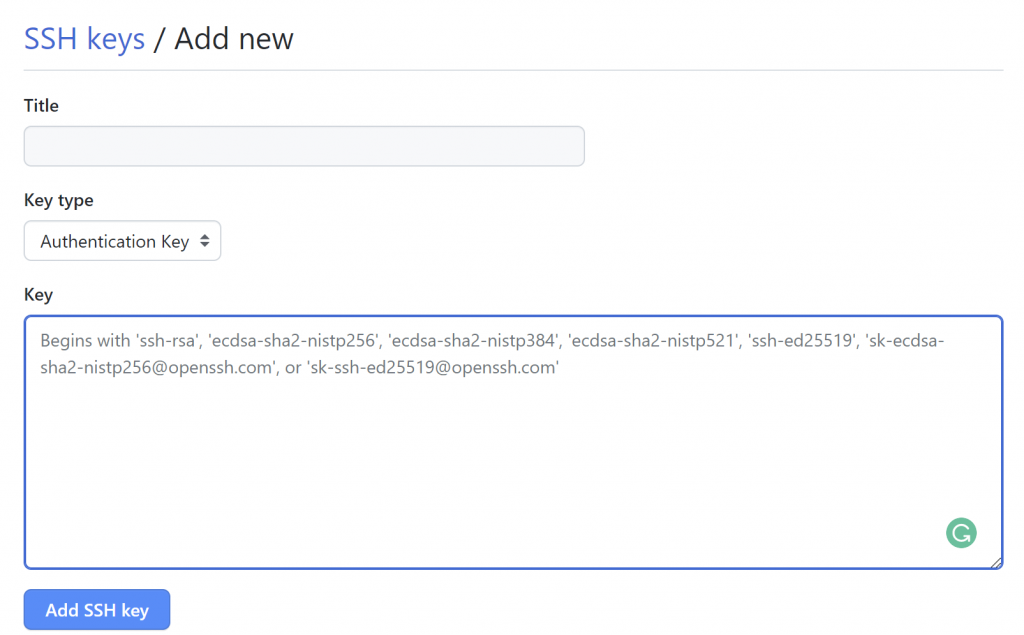
Provide a title, a friendly name to remember, and enter the public key and click Add SSH key.
Depending on your settings you might be prompted to re-authenticate or for MFA.
Now try cloning a repository from your Linux terminal. First copy the SSH URL of the repo:
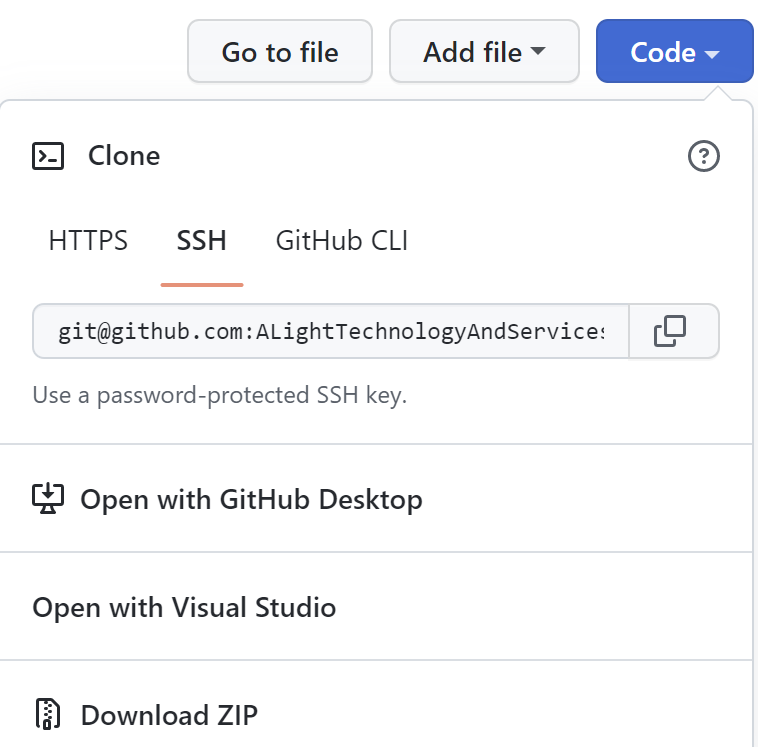
Then issue the following command on the Linux terminal to clone the main branch or a specific branch.
git clone <SSH_URL>
or
git clone --branch <BRANCH_NAME> <SSH_URL>Hoping this helps someone :).